Security Stack Solutions
Robust protection for your digital infrastructure through next-generation cybersecurity technologies.
Our Comprehensive Security Stack
Explore V-Tech’s end-to-end cybersecurity capabilities, designed to protect critical infrastructure and enable secure digital transformation across East Africa and beyond.

Next-Generation Firewalls & WAF
Protect your digital perimeter with next-generation firewalls and intelligent Web Application Firewalls (WAF). We design and deploy advanced firewall architectures that provide real-time traffic inspection, deep packet analysis, and intelligent threat blocking. Our WAF solutions secure web applications against common exploits like SQL injection and XSS, ensuring continuous protection without disrupting legitimate traffic.

Endpoint Protection & EDR
Defend every device in your environment with modern Endpoint Detection and Response (EDR) solutions. We deliver continuous endpoint visibility, behavioral analytics, and automated response to detect and contain threats at the device level. Whether on-premise or remote, our endpoint protection strategy ensures endpoints remain hardened against malware, ransomware, and zero-day attacks.
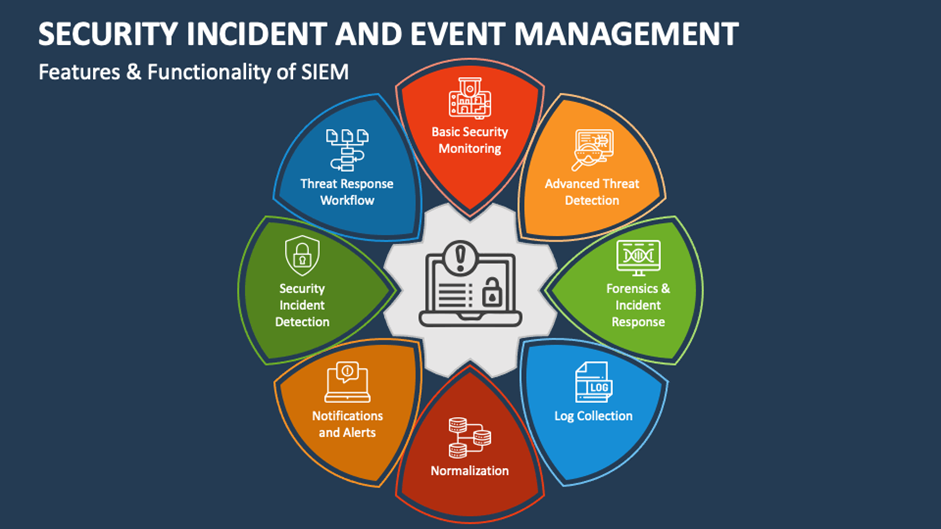
SIEM & Threat Detection
Achieve real-time visibility and actionable insights across your entire IT infrastructure. Our SIEM solutions centralize logs from firewalls, servers, endpoints, and applications, applying correlation rules and threat intelligence to detect suspicious behavior early. With advanced dashboards, alerting, and compliance reporting, we help security teams reduce detection time and respond faster to incidents.
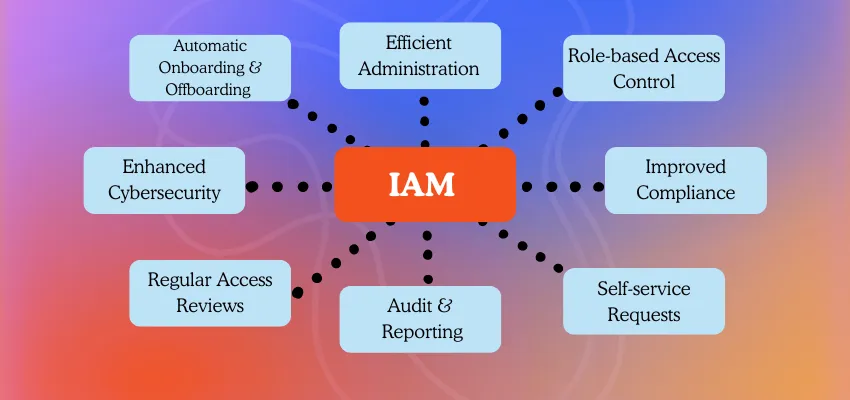
Identity & Access Management (IAM)
Control access to critical systems with centralized identity and access management. We implement MFA, SSO, role-based access, and automated user lifecycle management to ensure that only authorized users access the right resources at the right time. Our IAM solutions improve security while streamlining the user experience across the enterprise.
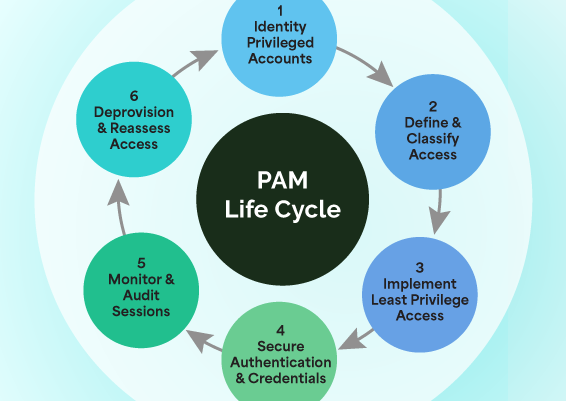
Privileged Access & Account Management (PAAM)
Secure the keys to your most sensitive systems through robust PAAM solutions. We provide privileged credential vaulting, just-in-time elevation, session recording, and granular policy enforcement. By controlling and monitoring privileged accounts, we help organizations prevent insider threats, reduce lateral movement, and meet stringent audit and compliance requirements.

Email & Cloud Security
Protect your communication and data flows across cloud and email environments. We deploy advanced threat filtering, phishing protection, DLP policies, and secure email gateways to stop targeted attacks and accidental leaks. Whether your workloads are on Microsoft 365, Google Workspace, or hybrid environments, our solutions safeguard critical data against evolving cloud-based threats.

15+
Why Organizations Choose V-Tech for Cybersecurity
V-Tech combines deep local market expertise with world-class cybersecurity partnerships to deliver solutions that are not only technically advanced, but also operationally relevant and compliant with East African regulatory environments.
- Deep experience delivering cybersecurity for banks, government, and telecoms, where security and compliance are mission-critical.
- Strong partnerships with global cybersecurity leaders like Fortinet, Palo Alto, IBM, and Thales.
- Solutions tailored to local regulatory and operational realities, ensuring practical, compliant implementations.
- End-to-end delivery from design and deployment to training, managed services, and ongoing optimization.
- Reliable post-deployment support and knowledge transfer to maintain a strong security posture over time.